Introduction to Hacking
Let’s try and understand Hacking , Types of Hacking and What are white hat hackers, grey hat hacker,black hat hackers .
Hacking is referred as unauthorized access to any Computer or system. To generalise the idea of Hacking , Hacking is being able to access a system you are not supposed to be accessed.
Who is a Hacker?
A hacker is a person who uses computer programming or any other Technical skill to solve a problem . There are many types of hacker , the dominant ones are white Hat Hackers , Grey hat hackers and Black Hat Hackers.
Different types of hackers are given below:
Hacker Types
Hackers can be broadly classified into three types. They are —
Black-hat Hackers
These are the people who gain unauthorized access to a system to withdraw funds or to achieve their own illegal goals. They are also known as Crackers.
White-hat Hackers
White hat hackers use the same skill as black hat hacker but the difference is they get permission before accessing someone's computer. The main purpose of white-hat hackers is to exploit the vulnerabilities that exist in a system. This type of hackers is also known as Ethical Hackers.
Grey-hat Hackers
These are a mixture of both White-hat hackers and Black-hat hackers, so they will hack into any system even if they do not have any permission to study the security of the system, but they will never have intentions of stealing money or damaging systems. In most cases, they will go ahead and tell the administrators of the system that they hacked and it was just for fun. But this is still illegal as they test the security of the systems which they do not own or have permission to do so.
Why should we learn Hacking?
1. We can secure our systems from being exploited by the Black Hat hackers.
2. Since the world is moving toward Cyber Wars , so there is allot more space to cover.
3. There are lots of job opportunities for Ethical hackers.
Types of Hacking
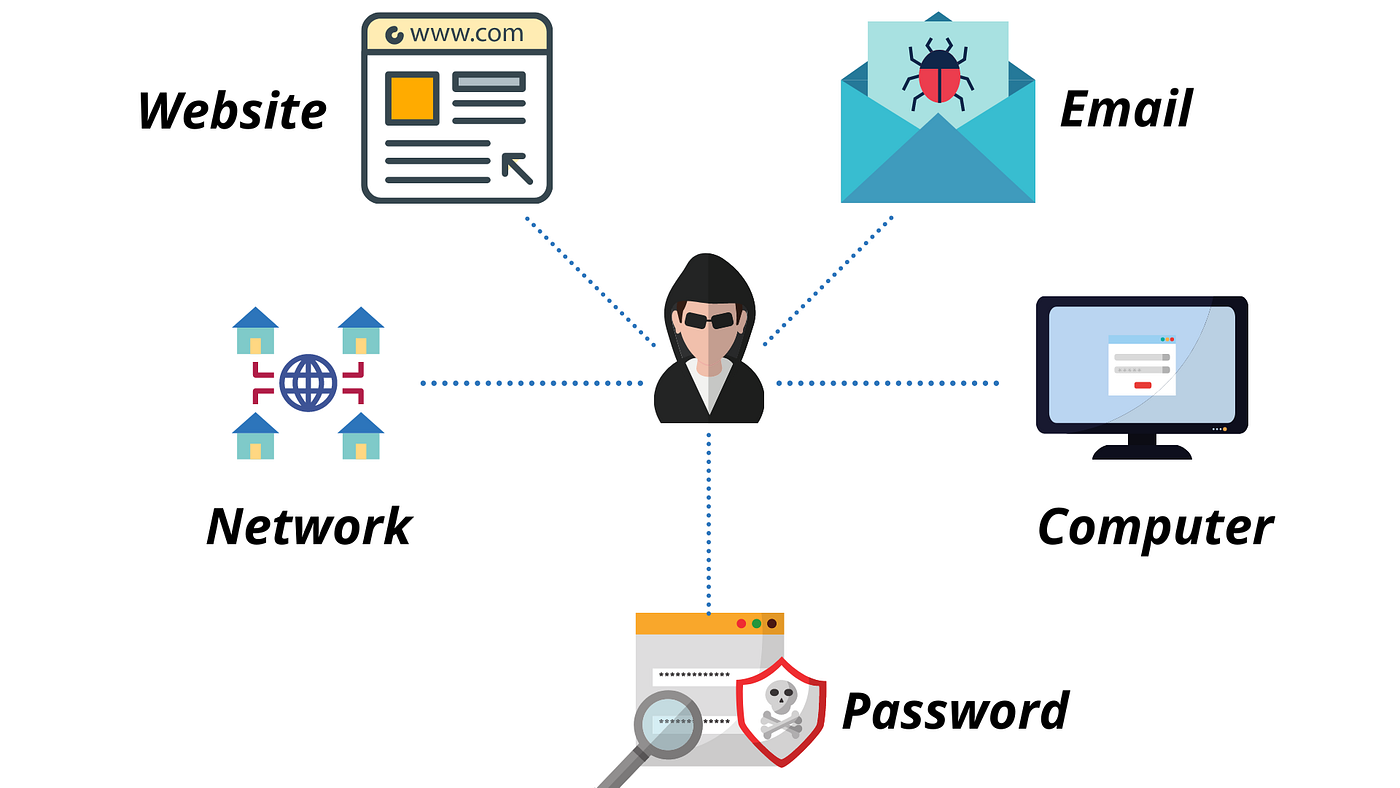
We can broadly classify hacking into five different classes based on what a hacker is trying to achieve. They are as follows:
1. Website Hacking
Website hacking can be defined as , taking unauthorized control over a website and its related software such as databases and other interfaces.
2. Network Hacking
Network Hacking is a way of gathering all the critical information about a network with an intent to harm the network and block its operations.
3. Email Hacking
Email Hacking is a way of gaining unauthorized access to an email account to spoof all the emails and send emails containing spam links and third-party threats.
4. Password Hacking
Password Hacking is a way of recovering secret passwords that are stored in a database or transferred over a network.
5. Computer Hacking
Computer Hacking is a way of gaining unauthorized access to a computer system by compromising its credentials.
Phases of Ethical Hacking
Ethical Hacking has 6 different phases. These are more likely to be the guidelines that are to be followed.
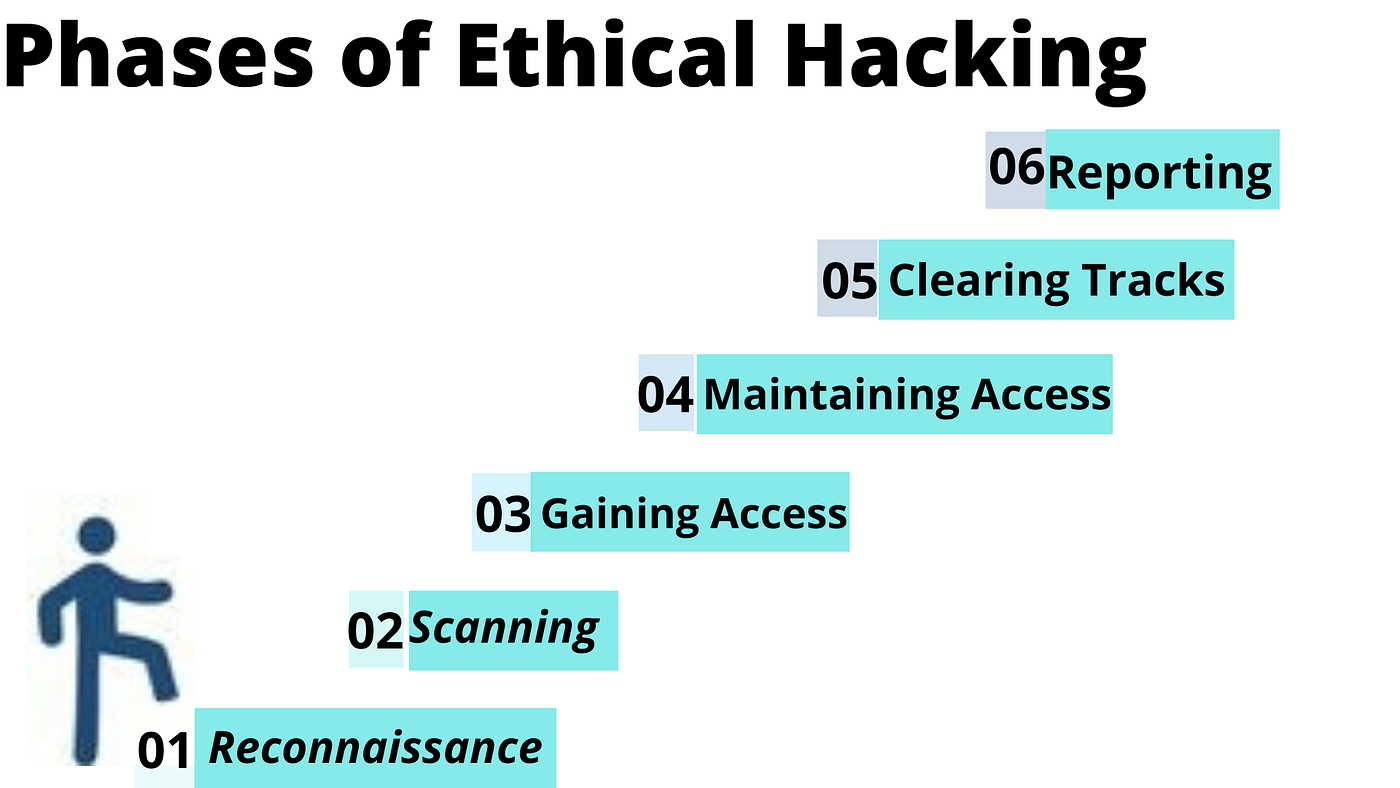
1. Reconnaissance
Reconnaissance is the process of gathering information. In this phase, the hacker tries to gather as much information as possible about the target system. The information like the network range, number of active devices, discovering the open ports and access points, etc.,
Reconnaissance is of two types. They are:
a. Active Reconnaissance:
Here, the hacker directly interacts with the target system to gain information. The information acquired can be relevant and accurate but the chances of getting detected are high. If you are detected then the system admin can take severe action against all your activities.
b. Passive Reconnaissance:
Here, the information is gathered without actually interacting with the target system.
2. Scanning
In this phase, the hacker tries to exploit all the vulnerabilities of the target system.
3. Gaining Access
The hacker tries to access the target system using the vulnerabilities that were exploited in the scanning phase without raising any alarms.
4. Maintaining Access
This is one of the most important phases of Ethical Hacking. In this phase, the hackers install various backdoors and payloads onto the target system. The payload is a term that is used for describing the activities that are performed on a system after gaining unauthorized access. These backdoors helps the hacker to access the system quickly in future.
5. Clearing Tracks
This is an unethical phase. In this, the hacker tries to delete all the logs of the activities that take place during the hacking process. Even ethical hackers performs this phase to understand how black hackers do that , so that they can be trained to fight back in need.
6. Reporting
Reporting is the last phase of Ethical hacking. A detailed report with all his findings, the tools used and various vulnerabilities exploited are given to specific organization or owner.
Some Terminology In Ethical hacking
Footprinting
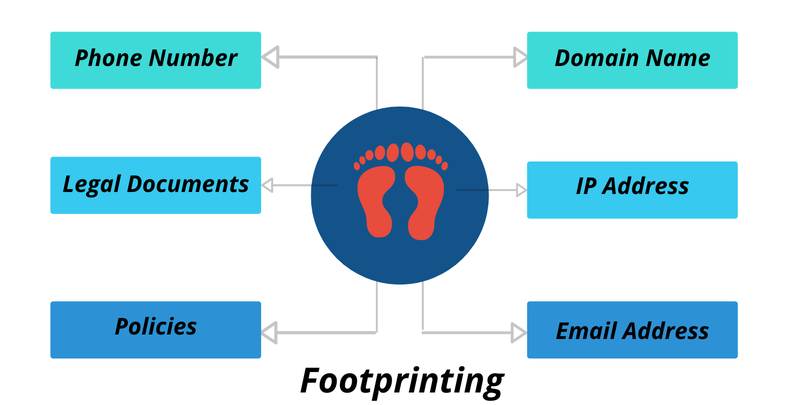
Footprinting is a part of the reconnaissance process which is used for gathering information about the target system. The information gathered is used to intrude into a target system or at least decide what types of attacks would be more suitable for the target system. Footprinting can be both passive and active.
Reviewing a company’s website is passive whereas attempting to gain access to sensitive information through various techniques comes under active reconnaissance.
Fingerprinting
Fingerprinting refers to any method that is used to determine the operating system that is being run on the target computer. Fingerprinting is also both active and passive.
Active fingerprinting is achieved by sending specially created packets to the target system, the response is then analyzed to determine the target OS.
Passive fingerprinting is achieved based on the sniffer traces from the remote system. Based on these sniffer traces of the packets, you can determine the operating system of the target host.
Conclusion :
In this article we covered all the basics to know about hacking. What are White Hat hackers , Black Hat Hackers and Grey Hat Hackers . Different steps used by a hacker to hack are also discussed .



1 Comments
Amazing . Easily explained.
ReplyDeleteIf you have any doubts let me know